A Recent Industrial Incident Gives Us Reasons To Worry
The Discovery In Dec 2017
 A piece of malicious software designed specifically to enable the damage or destruction of industrial equipment was reported discovered in an oil and gas installation in the middle East. Security firm FireEye identified a family of malware named Triton (also known as Trisis) which have been known to target equipment sold by Schneider Electric, and installed at oil and gas facilities, nuclear energy facilities or manufacturing plants.
A piece of malicious software designed specifically to enable the damage or destruction of industrial equipment was reported discovered in an oil and gas installation in the middle East. Security firm FireEye identified a family of malware named Triton (also known as Trisis) which have been known to target equipment sold by Schneider Electric, and installed at oil and gas facilities, nuclear energy facilities or manufacturing plants.
How Does The Malware Operate?
The Triton malware is designed to tamper with or even disable Schneider’s Triconex products, which are known as “safety-instrumented systems,” as well as “distributed control systems,” made by a separate company, used by human operators to monitor industrial processes. Safety-instrumented systems are expressly designed to remain isolated from production process monitoring control systems. Triton begins by parking itself in the DCS system – the heart of process control today in any industrial facility. Triton’s code is written to expressly disable Triconex safety measures, thereby blocking control loops that shut down key equipment that may generate dangerous process conditions.
According to Rob Lee, the founder of security firm Dragos Inc. -When Triton is installed in an industrial control system, the code looks for Schneider’s Triconex equipment, confirms that it can connect to it, and then begins injecting new commands into its operations. If those commands aren’t accepted by the Triconex components, it can crash the safety system.
The Good News
The Schneider Electric’s controller system is designed to be “fail-safe”. In other words, upon detection of a safety issue, it simply forces a domino “interlock” effect that would lead to other systems turning off as a safety measure, shutting down a major part of the plant’s operations. Industrial sites such as oil and gas and water utilities typically run multiple Safety Instrumented Systems to independently monitor critical systems to ensure they are operating within acceptable safety thresholds, and when they are not, the SIS automatically shuts them down. FireEye accidentally discovered Triton while responding to an incident in which a company’s SIS had entered a “fail-safe” state for no apparent reason.
The Bad News
Andrew Kling, director of cyber security and software practices for Schneider Electric – “We now know a real attack probably never took place. There was a mistake in the development of the malware that accidentally caused the Triconex to be tripped and taken to a safe state. As a result, this malware that was in development was uncovered”.
 FireEye noticed a “bug” in the payload delivery system of tthe malware. Blake Johnson, a consultant with Mandiant, a FireEye company – “The script was successful, but it backed itself out. We don’t believe that was supposed to happen” .
FireEye noticed a “bug” in the payload delivery system of tthe malware. Blake Johnson, a consultant with Mandiant, a FireEye company – “The script was successful, but it backed itself out. We don’t believe that was supposed to happen” .
A more likely intentional use would have been to keep the SIS running, while manipulating the DCS into disaster. If the attacker had a clear intent to launch a real attack, it could easily have exploited a better option of keeping the Safety Instrumented Systems running (as if normal) which manipulating the control system, because they would have controlled the DCS and caused significant damage. As Rob Lee puts it – “Everything could still appear to be working, but you’re now operating without that safety net. You could have explosions, oil spills, manufacturing equipment rip apart and kill people, gas leaks that kill people. It depends on what the industrial process is doing, but you could absolutely have dozens of deaths.” This implementation of Triton was likely a probe, or reconnaissance. That raises the possibility that it could be used again against targets.
Rob Lee, CEO and founder of Dragos – “The attack represents the first such incident to affect the OT engineering department, notes . It’s not targeting the operational level of HMIs or SCADA devices, but instead at the targeting engineering systems to change the logic on a system dedicated to protecting physical environments and people.”
Researchers say that the attackers had intimate knowledge of both Schneider products and their target industrial plant. While Schneider platforms run on mainstream PowerPC processors, they use proprietary hardware and software. The attackers also had knowledge of Schneider’s proprietary protocol for Tricon. Hackers would have needed to invest time and resources reverse-engineering Schneider code to map the systems and find the vulnerability.
Triton represents just the third-ever known malware specimen focused on damaging or disrupting physical equipment. The first was Stuxnet, widely assumed to have been designed by the NSA in partnership with Israeli intelligence. And late last year, a piece of sophisticated malware known as Industroyer, or Crash Override, targeted Ukraine’s power systems, triggering a brief blackout in the country’s capital of Kiev. That attack is widely believed to be the work of a team of Russian government hackers known as Sandworm who have waged a cyberwar on Ukraine since 2014.
NEW ATTACKS ON INDUSTRIAL INFRASTRUCTURE IN THE UNITED STATES
The Department of Homeland Security and the FBI issued a joint alert March 15 about “Russian government cyber actors” targeting U.S. critical infrastructure sectors, including energy, nuclear and commercial facilities.
 The DHS and FBI characterized this activity as a multi-stage intrusion campaign by Russian government cyber actors who targeted small commercial facilities’ networks where they staged malware, conducted spear phishing, and gained remote access into energy sector networks. After obtaining access, the Russian government cyber actors conducted network reconnaissance, moved laterally, and collected information pertaining to Industrial Control Systems (ICS).
The DHS and FBI characterized this activity as a multi-stage intrusion campaign by Russian government cyber actors who targeted small commercial facilities’ networks where they staged malware, conducted spear phishing, and gained remote access into energy sector networks. After obtaining access, the Russian government cyber actors conducted network reconnaissance, moved laterally, and collected information pertaining to Industrial Control Systems (ICS).
Targets included government entities and multiple U.S. critical infrastructure sectors, including the energy, nuclear, commercial facilities, water, aviation, and critical manufacturing sectors.
The attack campaign strategy covered two distinct categories of victims: staging and intended targets.
1. The initial victims are peripheral organizations such as trusted third-party suppliers with less secure networks, referred to as “staging targets” throughout this alert. The threat actors used the staging targets’ networks as pivot points and malware repositories when targeting their final intended victims.
2. Multi-phase attack themes specifically against intended target organizations.
Additional details available on this web-page of the United States Computer Emergency Readiness Team (US CERT)
According to James Lewis, a cybersecurity expert and vice president of the Center for Strategic and International Studies – “The Russians have been doing this for years,” Lewis said. “The change is that the U.S. government came out and said the Russians hacked the utilities.”
The government informed electric companies last summer that Russia undertook what DHS calls a “multistage intrusion campaign” against the utilities, using common hacking techniques such as malware and spear-phishing. The hackers were able to to gain access to at least one power plant’s control system. Scott Aaronson, vice president of security and preparedness at the Edison Electric Institute, which represents the nation’s electric companies, said U.S. power companies have tried to learn from that attack.
The new attribution—the first official confirmation by the U.S. of Russia’s effort—includes an accusation that the Kremlin was behind a group of sophisticated hackers known as “Dragonfly” that had penetrated energy company systems last year in ways that could be used to sabotage the U.S. electric grid.
Scott Aaronson, vice president of security and preparedness at the Edison Electric Institute, which represents the nation’s electric companies, said U.S. power companies have tried to learn from that attack.
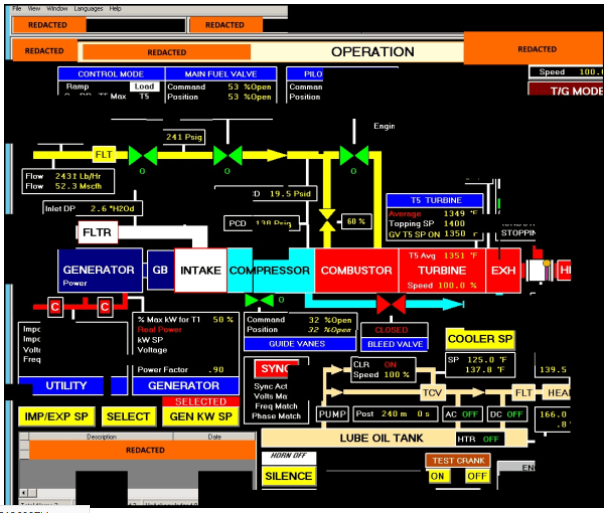
The Department of Homeland Security shared a reconstruct screenshot fragments of a human machine interface that was accessed. Shown below.